Data Connect Security
As of September 2025, Tableau Data Connect is no longer available for new deployments. We recommend that existing customers migrate their Data Connect deployment to Private Connect(Link opens in a new window) or Tableau Bridge(Link opens in a new window). Data Connect will be retired in the future.
Data Connect operates as a shared responsibility model. With this model, you supply the physical or virtual compute resources, and Tableau hosts and manages the Data Connect Kubernetes cluster on those resources. Tableau reduces the overhead of administration by remotely managing, monitoring, and maintaining the Kubernetes cluster. With the ability to perform remedial actions to enable continuous availability, Tableau eliminates the need to monitor traffic and connection status. In addition, to reduce latency and lower network congestion, Data Connect allows you to determine the data center, edge locations and environments that best meet your requirements for performance. In this model, Tableau is responsible for operating the Data Connect service securely and you are responsible for managing the infrastructure and networking layers.

Security designs
Data Connect applies the following security designs:
-
The Data Connect service is a control plane service and does not have access to your data. The underlying component for Data Connect service is Tableau Bridge.
-
To facilitate secure data transfer, Data Connect uses Tableau Bridge which leverages secure web sockets to establish persistent connections with Tableau Cloud.
-
The Data Connect service does not interact with database credentials or database access. Database credentials are securely stored on Tableau Cloud and are passed on to the Tableau Bridge client that is selected to perform the refresh.
-
All communication is initiated from behind your firewall and therefore does not require any additional explicit inbound firewall rules to manage exceptions.
Among other operations, the Bridge client is responsible for accessing your data and establishing secure web socket connections with Tableau Cloud. See Bridge Security.
Architecture
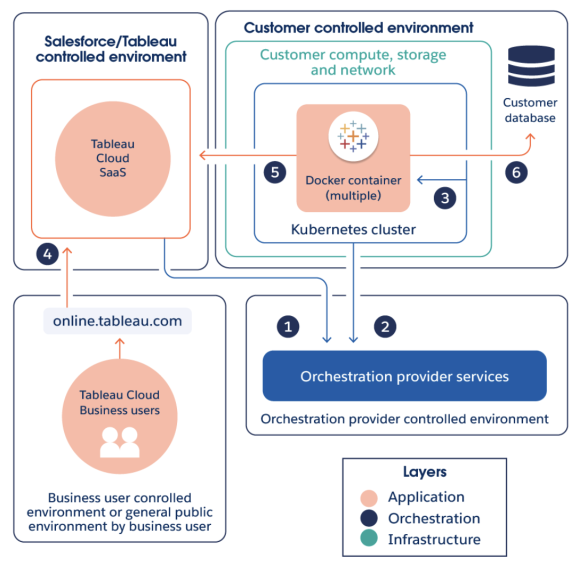
-
Tableau Cloud communicates with the Kubernetes orchestration service to deploy, monitor and manage the Kubernetes orchestration.
-
When you initialize Data Connect, a secure connection is established with the orchestration provider service over port 443.
-
After the service is configured, a Kubernetes cluster deploys a container(s) with Bridge client(s). These Bridge clients will be responsible for executing Tableau workloads.
-
Tableau Cloud users sign in to Tableau Cloud to interact with the Data Connect service.
-
On setup, Bridge clients initialize a connection with Tableau Cloud using HTTPS. After successful connection, Bridge clients initiate a secure, bidirectional communication to your Tableau Cloud environment using a WebSocket (wss://) connection.
-
Queries initiated from Tableau Cloud are run against your database to support end user analysis.
Security Layers
There are three layers to the Data Connect solution. The application that is installed in your infrastructure, the orchestration layer that is used to deploy and manage application(s) and the supporting network and hardware infrastructure.
-
Application layer: Database authentication, sending data to Tableau Cloud, and networking considerations, see Bridge Security.
-
Orchestration layer: See the section, Container orchestration, below.
-
Infrastructure layer: In the Data Connect shared responsibility model, the security of the infrastructure itself will be your responsibility. Security details about how the Data Connect orchestration layer interacts with your infrastructure are covered in the sections below.
Service configuration
During the configuration of Data Connect, you will be responsible for configuring and initiating the service from within your network. This process provides the correct level of access and specifies which Data Access nodes to integrate with your Tableau Cloud site. For details describing service configuration for Data Connect, see Step 1: Set up your cluster.
On initialization of the Data Connect solution, the following takes place:
-
Data Connect node health is validated.
-
A secure connection is established with the orchestration provider service over port 443.
-
Kubernetes operations software is downloaded and installed onto the computer. This software allows Tableau to remotely deploy and manage Data Connect.
-
Data Connect node information is queried over the secure connection to maintain the health of the service.
Your data is never transferred over the orchestration connection.
Tableau Cloud communication
All communication from your infrastructure to Tableau Cloud is initiated from behind your firewall. You do not have to manage additional exceptions.
For more information about Data Connect communication and your infrastructure configurations, see Networking specifications.
Tableau Cloud authentication
Data Connect creates authentication tokens that are used to secure Tableau Bridge's connection to Tableau Cloud. These tokens are site-specific and are used by the pool of Bridge clients that they are associated with. The tokens are stored in Kubernetes Secrets(Link opens in a new window) on the cluster, which is managed by Data Connect. The Bridge clients that are deployed on that cluster access these tokens to log in to Tableau Cloud, but the tokens are not stored on the clients.
To keep the Data Connect service running smoothly, Site Administrators for all sites using Data Connect need to refresh the token for their Pool every 90 days in Tableau Cloud. If the tokens aren't refreshed, Bridge clients in that pool will not be able to authenticate to the Tableau Cloud site and the jobs using that pool will fail.
Database authentication
You can find more details about Authentication in Bridge Security.
In the context of database authentication, it's important to understand that Data Connect only supports Bridge refresh schedules and does not support Bridge legacy schedules.
Container orchestration
The orchestration layer is exclusively a control layer and does not have access to the data layer and therefore does not interact with customer data. The only aspect of Data Connect that interacts with the data layer is the application installed on your infrastructure. This application is the Bridge client.
Security FAQ
What code is provisioned onto containers?
In addition to software required for Kubernetes operations (kops), Tableau Bridge for Linux for Containers is deployed. You must provision database drivers when you create the base image.
How can I manage detected vulnerabilities on the software deployed by Data Connect?
You supply all of the software deployed by Data Connect through the base image. To change the software deployed, you supply a new base image. The image will then be deployed to all Data Connect nodes in that pool.
What level of computer access does Data Connect require?
Data Connect requires administrative level access to your infrastructure. This access allows Tableau to update and maintain the service.
