Bridge Security
Tableau Bridge applies the following security designs:
- All communication is initiated from behind the private network firewall and therefore does not require you to manage additional exceptions.
- Data in transit, between Tableau Bridge and Tableau Cloud, is encrypted.
- Database credentials are stored on the computer using Windows credentials manager if the data source or virtual connection is set up to use Bridge legacy schedules. For refresh schedules, the credentials are passed on to the client that is selected to perform the refresh.
You can find more details about Bridge security in the sections below.
Transmission security
Note: Tableau Bridge uses port 443 to make outbound internet requests to Tableau Cloud and port 80 for outbound requests for certificate validation.
Tableau Bridge initiates a secure, bidirectional communication to your Tableau Cloud environment using a WebSocket (wss://) connection. The WebSocket connection is persistent and coordinates the data upload between Bridge and Tableau Cloud. All users are authenticated and authorized before the connection is made, and all inputs are validated to be from trusted sources within Tableau Cloud.
Authentication
There are two primary authentication points for Bridge: Tableau Cloud and private network data.
If the client is unlinked or you upgrade to a new version, you don't need to re-login. In this scenario, Bridge uses the existing token that is saved locally in the Windows credentials store.
If the client is shut down, or the Exit option on the Windows task bar is used, you are required to re-login and provide credentials. This creates a new refresh token which is saved to the Windows credentials store.
You can check the tokens in the credentials manager and check the Generic credentials for TABLEAU_CONNECTIONS_online.tableau.com.
Tableau Cloud
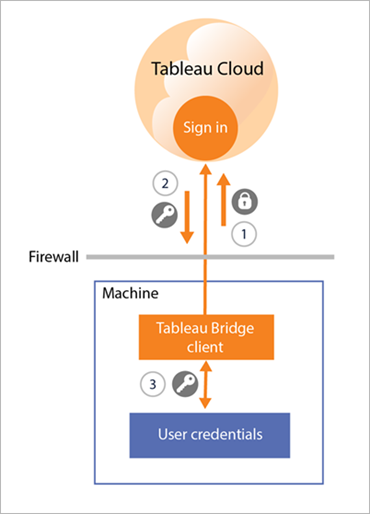
To connect to Tableau Cloud, a users Tableau Cloud credentials are entered through the Bridge client.
After 1) the credentials are entered, 2) an authorization token is returned by Tableau Cloud. The 3) token is stored on the computer where the client is running using the credentials manager of the Windows operating system. Bridge uses the token to perform various tasks such as downloading the refresh schedule information for an extract.
Private network data
To access private network data, some data sources or virtual connections require authentication using database credentials. Depending on the connection type of the content, the client handles database credentials in one of the following ways:
-
For live connections and extract connections that use refresh schedules, database credentials are sent at the time of the request and use a TLS 1.2 connection.
-
For extract connections that use Bridge legacy schedules, if the data source requires database credentials, these credentials must be entered in the client directly. The database credentials are stored on the computer using the credentials manager of the Windows operating system. The client sends the database credentials to the database, which is also behind the private network firewall, at the scheduled refresh time.
The client supports domain-based security (Active Directory) and user name/password credentials to access private network data.
Changes to private network firewall
The Bridge client requires no changes to the private network firewall. The client achieves this by making only outbound connections to Tableau Cloud. To allow outbound connections, the client uses the following protocols depending on the connection type used by the content:
-
For live connections and extract connections that use refresh schedules, secure WebSockets (wss://).
-
For extract connections that use Bridge legacy schedules, HTTP Secure (https://).
Access to private network data
Connections to private network data are initiated by the Bridge client on behalf of Tableau Cloud. The process by which the connection is initiated depends on the content type and connection type.
-
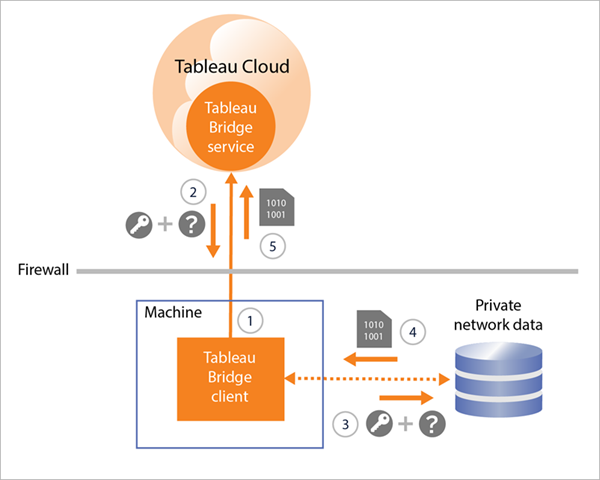
For data sources with live connections or virtual connections, the client 1) establishes a persistent connection to a Tableau Bridge service, which is the part of the client that resides on Tableau Cloud, using secure WebSockets (wss://). The client then waits for a response from Tableau Cloud before 2) initiating a live query to the private network data. The client 3) passes the query to the private network data, then 4) returns the private network data using 5) the same persistent connection.
-
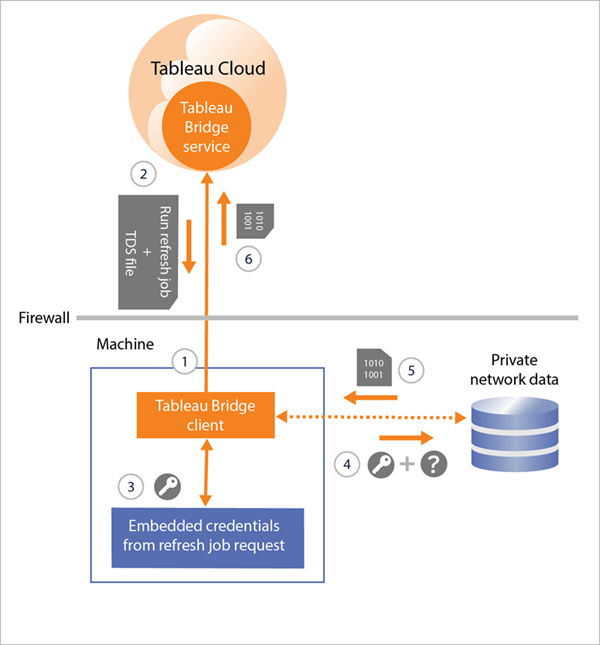
For data sources with extract connections that use refresh schedules, the client 1) establishes a persistent connection to a Tableau Bridge service, which is the part of the client that resides on Tableau Cloud, using secure WebSockets (wss://). The client then waits for a request from Tableau Cloud for new refresh schedules. When the client receives the requests, 2) the client contacts Tableau Cloud using a secure connection (https://) for the data source (.tds) files. 3/4) Then the client connects to the private network data using the embedded credentials that are included in the job request. The client 5) creates an extract of the data and then 6) republishes the extract to Tableau Cloud using the Tableau Bridge service. Steps 2-6 can be occurring in parallel to allow multiple refresh requests to happen.
-
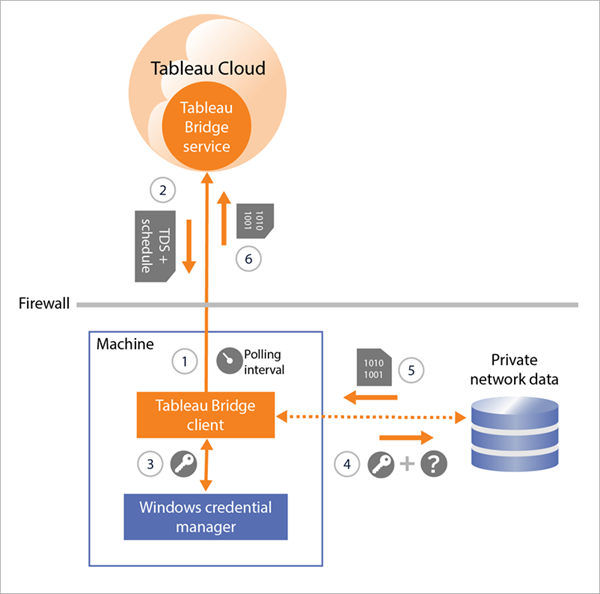
For data sources with extract connections that use Bridge legacy schedules, the client 1) contacts Tableau Cloud using a secure connection (https://) for new refresh schedules and data source (.tds) files. If 2) this information is available, at the scheduled time, 3/4) the client connects to the private network data using the stored credentials. The client 5) creates an extract of the data and then 6) republishes the extract to Tableau Cloud using a Tableau Bridge service. The Tableau Bridge service is a part of the client that resides on Tableau Cloud.
Forward proxy filtering
To ensure that your data is transmitted to Tableau Cloud only, we recommend implementing domain-based filtering on outbound connections (forward proxy filtering) from the Bridge client. After the initial outbound connection, communication is bidirectional.
Tableau Bridge doesn't support pass-through or manual proxy authentication.
The following list contains the partially qualified domain names that Bridge uses for outbound connections:
- *.online.tableau.com
- *.compute-1.amazonaws.com, Amazon VPC's public DNS hostname, which takes the form ec2-<public-ipv4-address>.compute-1.amazonaws.com, for the us-east-1 region
- *.compute.amazonaws.com, Amazon VPC's public DNS hostname, which takes the form ec2-<public-ipv4-address>.compute.amazonaws.com, for all other regions (outside of us-east-1)
- (Optional) *.salesforce.com, id.tableau.com, and identity.idp.tableau.com if multi-factor authentication (MFA) with Tableau authentication (Tableau with MFA) is enabled for your site and your environment is using proxies that prevent clients from accessing other necessary services
- (Optional) crash-artifacts-747369.s3.amazonaws.com, used for receiving crash dump reports
- (Optional) s3-us-west-2-w.amazonaws.com, used for receiving crash dump reports
- (Optional) s3-w-a.us-west-2.amazonaws.com, used for receiving crash dump reports
- (Optional) bam.nr-data.net, used for New Relic's web analytic platforms
- (Optional) js-agent.newrelic.com, sends performance data to New Relic
