Configure Azure AD for OAuth and Modern Authentication
The Azure Synapse, Azure SQL Database, Azure Databricks, Azure Data Lake Gen2, OneDrive and SharePoint Online, and SharePoint Lists (JDBC) connectors support authentication through Azure AD by configuring an OAuth client for Tableau Server.
Note: Single-use refresh tokens (sometimes called rolling refresh tokens or refresh token rotation) are not supported for OAuth connections to Tableau at this time. Support for these tokens is planned for a future release.
Note: OAuth support for Azure AD is only supported with Microsoft SQLServer driver 17.3(Link opens in a new window) and later.
Step 1: Register OAuth client for Azure
Follow the steps below to register and configure an OAuth application for Azure under a specific Azure tenant.
- Sign in to the Azure portal.
- If you have access to multiple tenants, select the tenant in which you want to register an application.
- Search for and select Azure Active Directory.
- Under Manage, select App registrations,and then select New registration.
- Enter “Tableau Server OAuth”, or similar value as the Name.
- Under the Supported account types field in the app registration page, select who can use this application.
- Under Redirect URI (optional) field, choose Web and then enter the internet address of your server appended by the string,
/auth/add_oauth_token. - Select Register. After the registration completes, the Azure portal displays the app registration's Overview pane, which includes its Application (client) ID. Also referred to as Client ID, this value uniquely identifies your application in the Microsoft identity platform.
- Copy the ID; it will be used as the
[your_client_id]field in the following steps. - Select Certificates & secrets in the left bar, and then choose New client secret.
- Add a description of the secret.
- Select Client secret lifetime.
- Choose Add and then copy the secret value. The secret value will be used as
[your_client_secret_value]in the following steps. - Select API permissions on the left bar.
- Choose Add permissions.
- Select Microsoft Graph.
- Choose Delegated permissions.
- Under Select permissions, select all OpenId permissions (email, offline_access, openid and profile).
- Choose Add permissions.
- Add additional permissions. Follow the steps below for the connector(s) that you are enabling:
- Azure SQL database
- Click Add a permission.
- Select My APIs.
- Click Azure SQL Database and then Delegated permissions.
- Select user_impersonation and then click Add permissions.
- OneDrive and SharePoint Online
- Click Add a permission.
- Select Microsoft Graph.
- Click Delegated permissions.
- Under Select permissions, in the filter search box, enter and then add the following permissions:
- Files.Read.All
- Sites.Read.All
- User.Read
- SharePoint lists (JDBC)
- Click Add a permission.
- Select Microsoft Graph.
- Click Delegated permissions.
- Under Select permissions, in the filter search box, enter and then add User.Read permission.
- Click Add a permission again.
- Select SharePoint.
- Click Delegated permissions.
- Expand the AllSites section and then select and add the AllSites.Manage permission.
- Azure SQL database
Note: If you want to use the Client ID & Client Secret Value of your application for accounts under a different tenant, choose the second option (Multi-tenant).
For example: https://your_server_url.com/auth/add_oauth_token
Step 2: Configure Tableau Server for Azure
Configuring Tableau Server requires running a Tableau Server Manager (TSM) command. Azure Data Lake Storage Gen2 requires a different set of commands than the common command that is run for Azure Synapse, Azure SQL Database or Databricks.
Configure default OAuth client for Azure Data Lake Storage Gen2
To configure Tableau Server for Data Lake Storage Gen2, you must have the following configuration parameters:
- Azure OAuth client ID: The client ID is generated from the procedure in Step 1. Copy this value for
[your_client_id]in the first tsm command. - Azure OAuth client secret value: The client secret value is generated from the procedure in Step 1. Copy this value for
[your_client_secret_value]in the second tsm command. - Tableau Server URL: Enter your Tableau Server URL, such as
https://myco.com. Copy this value for[your_server_url]in the third tsm command.
Run the following tsm commands to configure Tableau Server OAuth for Azure Data Lake Storage Gen2:
tsm configuration set -k oauth.azuredatalake_storage_gen2.client_id -v [your_client_id] --force-keystsm configuration set -k oauth.azuredatalake_storage_gen2.client_secret -v [your_client_secret_value] --force-keystsm configuration set -k oauth.azuredatalake_storage_gen2.redirect_uri -v [your_server_url]/auth/add_oauth_token --force-keystsm pending-changes apply
Configure default client for Azure Synapse, Azure SQL Database or Databricks
To configure Tableau Server, you must have the following configuration parameters:
- Azure OAuth client ID: Generated from the procedure in Step 1. Copy this value for
[your_client_id]in the tsm command. - Azure OAuthClient secret value: Generated from the procedure in Step 1. Copy this value for
[your_client_secret_value]in the second tsm command. - Tableau Server URL: This is your Tableau Server URL, such as
https://myco.com. - Configuration ID: The value for the
oauth.config.idparameter in the following tsm command. Valid values:- Azure Synapse:
azure_sql_dw - Azure SQL Database:
azure_sqldb - Databricks:
databricks
- Azure Synapse:
Run the following tsm commands to configure Azure AD for Azure Synapse, Azure SQL Database or Databricks. For example, to set up Azure Synapse:
tsm configuration set -k oauth.config.clients -v "[{\"oauth.config.id\":\"azure_sql_dw\", \"oauth.config.client_id\":\"[your_client_id]\", \"oauth.config.client_secret\":\"[your_client_secret_value]\", \"oauth.config.redirect_uri\":\"[your_server_url]/auth/add_oauth_token\"}]" --force-keys
tsm pending-changes apply
Configure a default OAuth client for OneDrive and SharePoint Online
To configure Tableau Server for OneDrive and SharePoint Online, you must have the following configuration parameters:
- Azure OAuth client ID: The client ID is generated from the procedure in Step 1. Copy this value for [your_client_id] in the first tsm command.
- Azure OAuth client secret value: The client secret value is generated from the procedure in Step 1. Copy this value for [your_client_secret_value] in the second tsm command.
- Tableau Server URL: This is your Tableau Server URL, such as
https://myco.com. Copy this value for [your_server_url] in the third tsm command.
Run the following tsm commands to configure Tableau Server OAuth for OneDrive and SharePoint Online:
tsm configuration set -k oauth.onedrive_and_sharepoint_online.client_id -v [your_client_id] --force-keystsm configuration set -k oauth.onedrive_and_sharepoint_online.client_secret -v [your_client_secret_value] --force-keystsm configuration set -k oauth.onedrive_and_sharepoint_online.redirect_uri -v [your_server_url]/auth/add_oauth_token --force-keystsm pending-changes apply
Configure a default OAuth client for SharePoint Lists (JDBC)
To configure Tableau Server for SharePoint Lists (JDBC), you must have the following configuration parameters:
- Azure OAuth client ID: The client ID is generated from the procedure in Step 1. Copy this value for [your_client_id] in the first tsm command.
- Azure OAuth client secret value: The client secret value is generated from the procedure in Step 1. Copy this value for [your_client_secret_value] in the first tsm command.
- Tableau Server URL: This is your Tableau Server URL, such as
https://myco.com. Copy this value for [your_server_url] in the first tsm command.
Run the following tsm commands to configure Tableau Server OAuth SharePoint Lists (JDBC):
tsm configuration set -k oauth.config.clients -v "[{\"oauth.config.id\":\"cdata_sharepoint\", \"oauth.config.client_id\":\"[your_client_id]\", \"oauth.config.client_secret\":\"[your_client_secret_value]\", \"oauth.config.redirect_uri\":\"[your_server_url]/auth/add_oauth_token\"}]" --force-keystsm pending-changes apply
Configure a default OAuth client for OneDrive (deprecated)
To configure Tableau Server for OneDrive (deprecated), you must have the following configuration parameters:
- Azure OAuth client ID: The client ID is generated from the procedure in Step 1. Copy this value for [your_client_id] in the first tsm command.
- Azure OAuth client secret value: The client secret value is generated from the procedure in Step 1. Copy this value for [your_client_secret_value] in the second tsm command.
- Tableau Server URL: This is your Tableau Server URL, such as
https://myco.com. Copy this value for [your_server_url] in the third tsm command.
To continue run the following tsm commands to configure Tableau Server OAuth for OneDrive (deprecated):
tsm configuration set -k oauth.onedrive.client_id -v [your_client_id] --force-keystsm configuration set -k oauth.onedrive.client_secret -v [your_client_secret_value] --force-keystsm configuration set -k oauth.onedrive.redirect_uri -v [your_server_url]/auth/add_oauth_token --force-keystsm pending-changes apply
Server Restart Scenarios
After you configure a default OAuth client, the following scenarios can occur.
- A restart prompt appears if the pending changes require a server restart.
- You can suppress the prompt using the
--ignore-promptoption, but this doesn’t stop the restart. - If the changes don't require a restart, the changes are applied without a prompt. For more information, see tsm pending-changes apply.
Setting multiple connectors
If you have multiple connectors to set, you must include all of them in a single command. For example:
tsm configuration set -k oauth.config.clients -v "[{\"oauth.config.id\":\"azure_sql_dw\", \"oauth.config.client_id\":\"[your_client_id]\", \"oauth.config.client_secret\":\"[your_client_secret_value]\", \"oauth.config.redirect_uri\":\"[your_server_url]/auth/add_oauth_token\"}, {\"oauth.config.id\":\"azure_sqldb\", \"oauth.config.client_id\":\"[your_client_id]\", \"oauth.config.client_secret\":\"[your_client_secret_value]\", \"oauth.config.redirect_uri\":\"[your_server_url]/auth/add_oauth_token\"}, {\"oauth.config.id\":\"databricks\", \"oauth.config.client_id\":\"[your_client_id]\", \"oauth.config.client_secret\":\"[your_client_secret_value]\", \"oauth.config.redirect_uri\":\"[your_server_url]/auth/add_oauth_token\"}]" --force-keys
tsm pending-changes apply
Configure custom OAuth for a site
You can configure custom Azure Data Lake Storage Gen2, Azure Synapse, Azure SQL Database, Databricks OAuth, OneDrive and SharePoint online, and Sharepoint Lists (JDBC) clients for a site.
Consider configuring a custom OAuth client to 1) override an OAuth client if configured for the server or 2) enable support for securely connecting to data that requires unique OAuth clients.
When a custom OAuth client is configured, the site-level configuration takes precedence over any server-side configuration and all new OAuth credentials created use the site-level OAuth client by default. No Tableau Server restart is required for the configurations to take effect.
Important: Existing OAuth credentials established before the custom OAuth client is configured are temporarily usable but both server administrators and users must update their saved credentials to help ensure uninterrupted data access.
1: Prepare the OAuth client ID, client secret value and redirect URL
Before you can configure the custom OAuth client, you need the information listed below. After you have this information prepared, you can register the custom OAuth client for the site.
OAuth client ID and client secret value: First register the OAuth client with the data provider (connector) to retrieve the client ID and secret value generated for Tableau Server.
Redirect URL: Note the correct redirect URL. You will need this during the registration process in Step 2 below.
https://<your_server_name>.com/auth/add_oauth_token
For example, https://example.com/auth/add_oauth_token
2: Register the OAuth client ID and client secret
Follow the procedure described below to register the custom OAuth client to the site.
Sign in to your Tableau Server site using your admin credentials and navigate to the Settings page.
Under OAuth Clients Registry, click the Add OAuth Client button.
Enter the required information, including the information from Step 1 above:
For Connection Type, select the connector whose custom OAuth client you want to configure.
OAuth Instance URL is required if multiple OAuth clients are being registered. Otherwise, it is optional.
For Client ID, Client Secret and Redirect URL, enter the information you prepared in Step 1 above.
Click the Add OAuth Client button to complete the registration process.
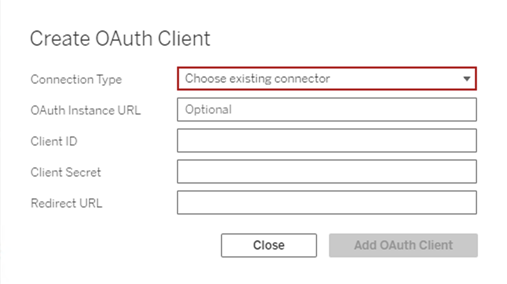
(Optional) Repeat step 3 for all supported connectors.
- Click the Save button at the bottom or top of the Settings page to save changes.
3: Validate and update saved credentials
To help ensure uninterrupted data access, you (and your site users) must delete the previously saved credentials and add it again to use the custom OAuth client for the site.
Navigate to your My Account Settings page.
Under Saved Credentials for Data Sources, do the following:
Click Delete next to the existing saved credentials for the connector whose custom OAuth client you configured in Step 2 above.
Next to connector name, click Add and follow the prompts to 1) connect to the custom OAuth client configured in Step 2 above and 2) save the latest credentials.
4: Notify users to update their saved credentials
Make sure you notify your site users to update their saved credentials for the connector whose custom OAuth client you configured in Step 2 above. Site users can use the procedure described in Update saved credentials to update their saved credentials.
