Extension Security - Best Practices for Deployment
These best practices are for IT officers and administrators, Tableau server and site administrators, and anyone who's interested in adopting the use of dashboard and viz extensions with Tableau. Extensions provide vast opportunities to extend and customize the use of Tableau to fit the analytic needs of each customer. This extensibility should always include the appropriate considerations toward the security of their data and business. The best practices are intended for deployments that have a mix of users who are on Tableau Desktop and Tableau Server or Tableau Cloud.
Security for extensions in Tableau
Extensions are web applications that extend the functionality of the dashboard or add new visualizations to Tableau. These solutions can be handled directly by Tableau or served completely as third-party custom services. These services can be hosted either within your own network, or provided by an external provider outside your network. Extensions interact with other components in the workbook and create an integrated experience for the end user using Tableau analytics content. To provide this integrated experience, Extensions access the visible summary data used in the workbook. Under specific configuration, they can also access the underlying data in the workbook if needed. This access and interaction level is enabled by the Tableau Extension API, which is designed and supported as a part of the Tableau platform.
Tableau supports two standards for extensions:
Tableau Trusted Extensions
To support the broad use of extensions across its community, Tableau manages services to help serve extensions for use at scale. These extensions can be built and maintained by Tableau directly as platform features, or by Salesforce or Tableau partner developers that work closely with Tableau’s product teams to jointly deploy solutions for broad community use through Tableau Exchange. Tableau Trusted Extensions are always hosted on Tableau infrastructure, managed and governed by the Tableau product and development team. Tableau tests and reviews each extension before it’s deployed or updated. Tableau has strict requirements to only permit communication between user clients and the access-controlled Tableau extension hosts. With this design, Tableau can provide standards on common extensions needs that can be useful for its community. To meet this standard, Tableau employs different solutions to deliver towards this goal:
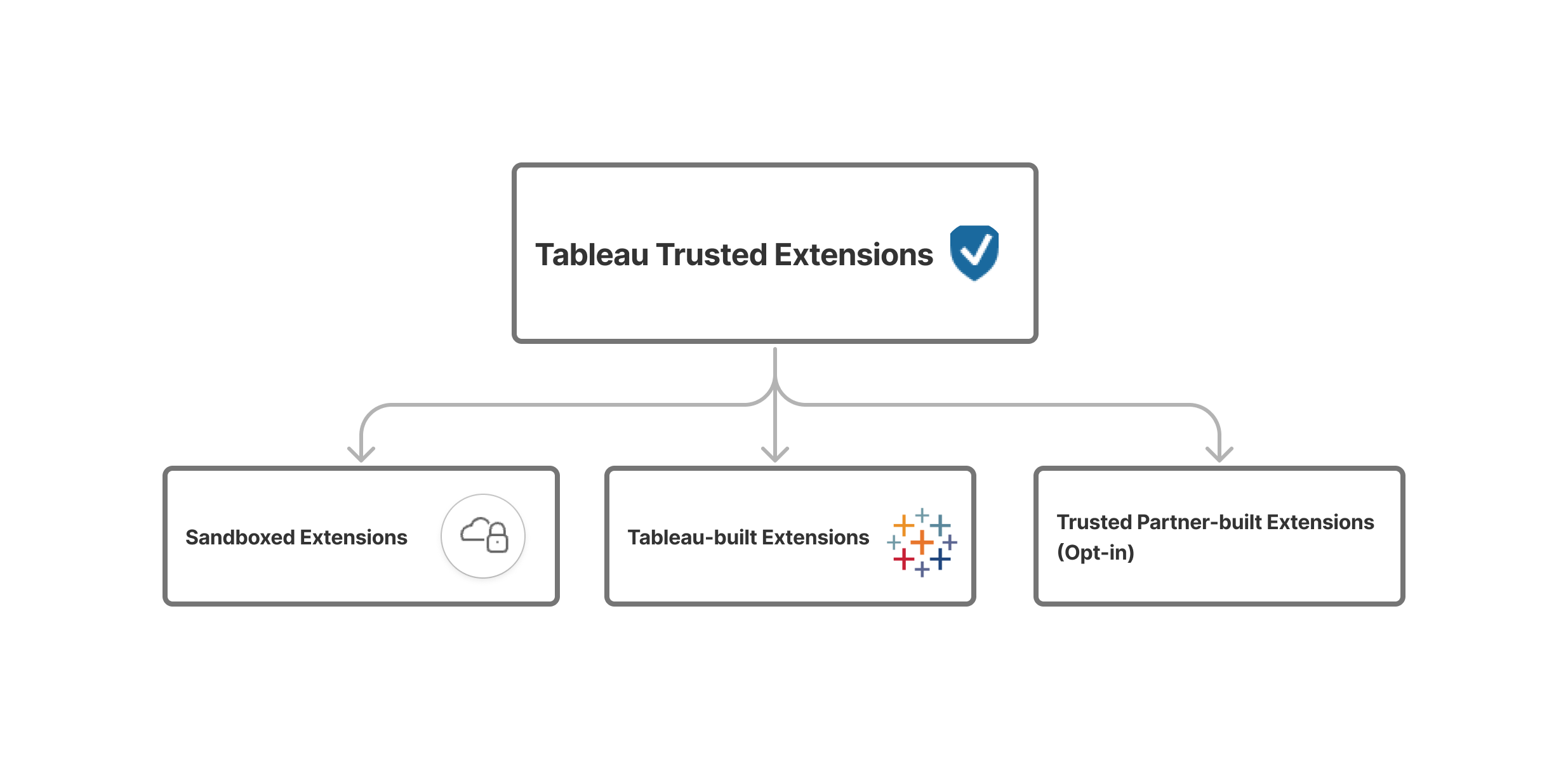
Sandboxed extensions
Tableau hosts Sandboxed extensions, which run in a protected environment specifically configured to eliminate the risk of data exfiltration.
The Tableau Sandboxed extensions host is blocked from any other resource or service on the web. A Sandboxed extension can query data in the workbook using the Extensions API, but it can't send that data anywhere outside the sandbox. The results of the query are on the client computer (in the browser) and can't be sent anywhere. Restricted access ensures that only Tableau employees manage all updates to Sandboxed extensions and are the only ones to access this extension host. The Sandboxed extensions environment and hosting service has undergone penetration testing by a 3rd-party consultant. Sandboxed extensions are enabled for use by default and enabled for Tableau Public use.
Tableau-built extensions
Tableau-built extensions are hosted by Tableau. Specifically, these extensions are built and maintained by the Tableau development team as platform features. Like other features built by Tableau, Tableau-built extensions undergo Salesforce SDLC standards. These extensions are designed to pass JavaScript to the client computer. This allows the extension to be rendered and processed by the client. These features are supported directly by the Tableau team and deployed through the same Tableau Trusted host infrastructure. Tableau-built extensions are enabled for use by default and enabled for Tableau Public use.
Tableau Trusted partner-built extensions (Opt In)
Tableau Trusted partner-built extensions are developed by third-party partner developers, but reviewed and hosted by Tableau. By managing deployment for partner developers (many of whom are also longstanding community leaders), these new solutions can be delivered jointly between Tableau and the third-party Tableau Exchange Partner. Tableau tests each third-party solution (and each update) before they are deployed for production use. This includes functional and network communication testing, as well as automated code scans for vulnerabilities to address. Like other Tableau Trusted extensions, these extensions only allow communication between the user client and the Tableau host. Direct access to the host is controlled and limited only to Tableau employees. While Tableau can't directly make changes or apply fixes to these third-party solutions, the service uptime and availability is governed by Tableau. Tableau Trusted partner-built extensions require administrators to enable them for use, but are generally recommended and have been enabled for Tableau Public use.
Network-enabled extensions
Network-enabled extensions are extensions not managed by Tableau. They can be hosted on web servers that are located inside or outside your local network and have full access to the web. This allows network-enabled extensions to address more specific integration needs or custom deployment goals outside of Tableau’s standards. Network-enabled extensions can connect with other applications and services to offer new integrated capabilities to Tableau. This includes non-Tableau natural language generation or support for write-back scenarios. Network-enabled extensions have full access to the web, which means that they can offer rich features and experiences by being able to connect to outside resources. However, as they might communicate with additional services and aren't managed by Tableau, we encourage you to evaluate Network-enabled extensions before deploying or adopting at scale.
Locally deployed Network-enabled extensions
Extensions can support deployment flexibility, such as running extensions locally within a local network. This is particularly useful for deployments that have air-gapped network requirements, or for organizations that prefer to manage their own extensions. For example, internal developers can build custom extensions that meet specific deployment needs. Network-enabled extensions support the goal of self-deployment. Because these local extensions run on non-Tableau hosts and undergo their own custom release definitions, we encourage you to work with your developers to plan appropriately on how this internal extension resource and relevant process is managed for users in your deployment. By design, network-enabled extension architecture allows full access to the web; so it's incumbent on customers to develop their own review process to ensure that extensions specifically only communicate with allowed web resources and have appropriate cybersecurity safeguards to protect against risk. Local Network-enabled extensions are required to be added to the deployment extension safe list by Tableau administrators before they are allowed for use. These local solutions aren't used in Tableau Public.
Third-party provider-managed Network-enabled extensions
Network-enabled extension architecture also allows extensions to be served by a trusted third-party provider, such as directly by a Tableau partner that you’ve established a formal vendor relationship with. In these situations, a network-enabled extension, not managed by Tableau, lets providers offer direct production support or custom services. When handled in a trusted manner, this can streamline and expand on the customization for Tableau supported by a reputable provider. We recommend customers work with third-party providers directly for a more thorough understanding of how a provider’s development practices, extension code design, and security meets their internal guidelines. These Network-enabled extensions are required to be added to the deployment extension safe list by Tableau administrators before they are allowed for use. On rare occasions, these solutions are enabled to be used in Tableau Public as unique exceptions for community goals.
Risk considerations with Network-enabled extensions
Because extensions are web applications there's the potential that a Network-enabled extension could be vulnerable to certain types of malicious attacks, which in turn could present a risk to your computer or data. The Open Web Application Security Project(Link opens in a new window) (OWASP) annually identifies the most critical web application security risks. These risks include the following:
- SQL injection
- Cross-site scripting (XSS)
- Sensitive data exposure
These risks could compromise the extension if the developers of the extension don't properly validate and handle user inputs, or if they generate dynamic queries to access sensitive databases. As you evaluate the extensions that you want to allow in Tableau, be sure to consider how they manage authentication, data access, or user input, and how they mitigate security risks.
Mitigating security threats with Network-enabled extensions
Understanding what an extension does is a first step to identifying the risks for your enterprise. Often, a dashboard or viz extension doesn’t access the underlying data in the workbook and all the JavaScript code runs in the context of the browser running on the user’s computer. In these cases, no data leaves the computer, even though the extension might be hosted on a third-party site outside of your domain. Some extensions allow you to connect Tableau with other applications you have already deployed in your domain.
Tableau provides security measures and security requirements for extensions. These requirements are enabled for Tableau Desktop, Tableau Server, and Tableau Cloud.
- All extensions must use the HTTP Secure (HTTPS) protocol.
- By default, anyone using a dashboard with a Network-enabled extension will be prompted and asked to allow the extension permission to run. The extension must request permission if it accesses the underlying data.
- To run on Tableau Server or Tableau Cloud, the URL of the Network-enabled extension must be added to a safe list. The server administrator manages this list for Tableau Server; the site administrator manages this list for Tableau Cloud.
- On Tableau Server and Tableau Cloud, the server or site administrator (respectively) can control whether the prompt appears for each Network-enabled extension.
For more information, see Manage Dashboard and Viz Extensions in Tableau Server.
Manage extensions using Tableau
Extensions provide a way to add unique features to dashboards and new visualizations to worksheets. You can use extensions to directly integrate the dashboard with applications outside of Tableau. While extensions open up a world of possibilities, there are instances where you need or want to maintain control of how extensions are deployed in your company or enterprise. In this respect, extensions are no different from any other software that you intend to use. Before you deploy software applications in your company you should thoroughly test and verify that the software works as expected and is secure. The same is true for extensions.
First, determine what level of access your users should have, and identify the extensions you want to use (or conversely, the extensions you don’t want to use). Then use the controls and features within Tableau to restrict and curate the dashboard and viz extensions users have access to.
- Do you need to restrict who can add or use extensions in Tableau Desktop? See Recommendations for Tableau Desktop
- Do you need to restrict or control the extensions your users have access to? See Recommendations for Tableau Server and Tableau Cloud.
Recommendations for Tableau Desktop
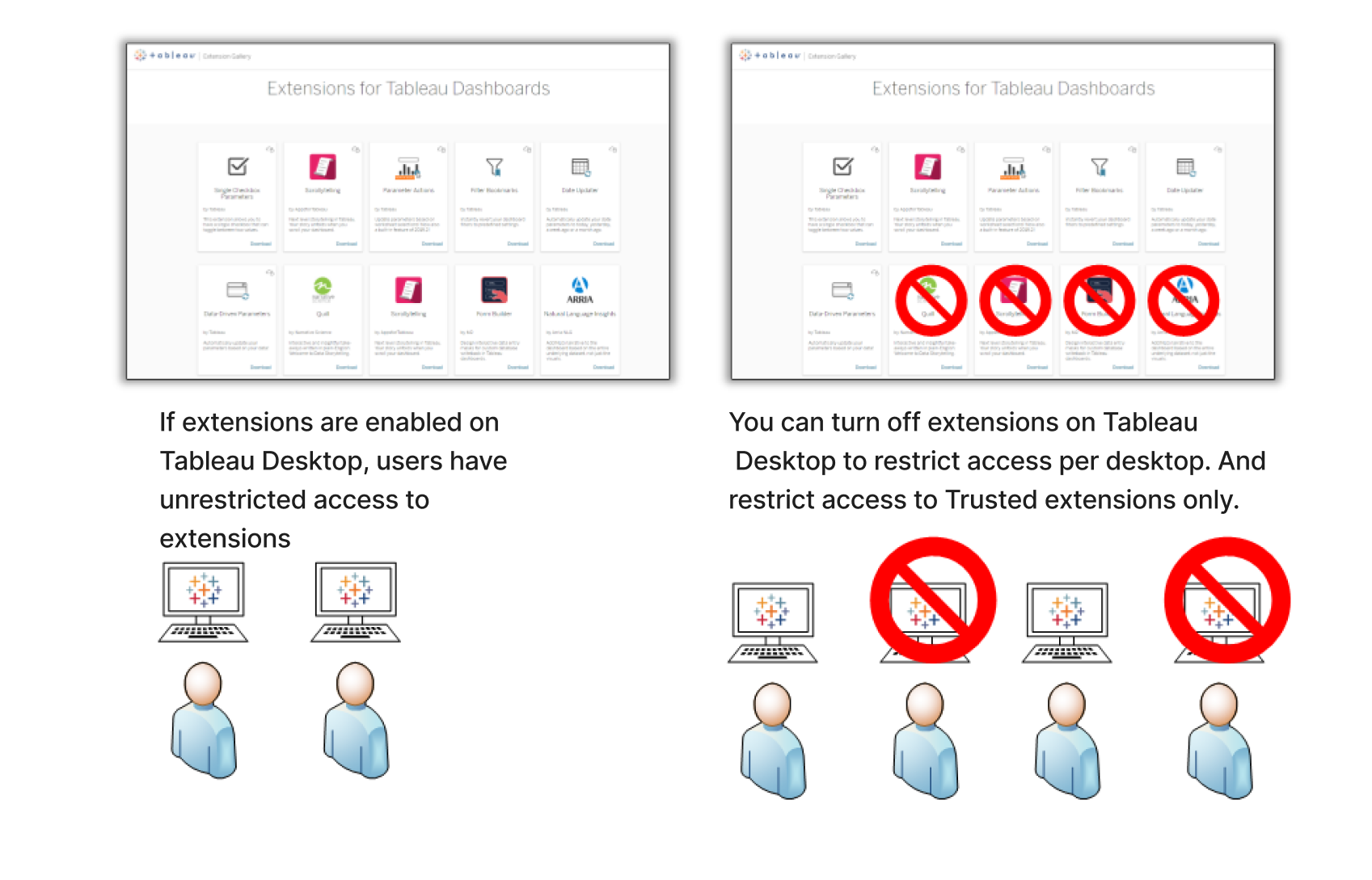
You have a range of options for deploying Tableau Desktop in your company. You can allow unrestricted access to extensions, or you can put limits and restrictions on who has access to extensions and under what circumstances.
By default, Tableau Desktop users have unrestricted access to Tableau Trusted extensions and Network-enabled extensions. Tableau provides five options that can be used in any permutation during installation to change the default settings.
- Turn off all extensions (
DISABLEEXTENSIONS) - Turn off Network-enabled extensions (
DISABLENETWORKEXTENSIONS). -
Turn off Sandboxed extensions (
DISABLESANDBOXEXTENSIONS). -
Turn off Tableau built extensions (
DISABLETABTRUSTEDEXTENSIONS). -
Turn off Tableau Trusted Partner-built extensions (
DISABLE3PTRUSTEDEXTENSIONS).
Note: You can change these settings after Tableau Desktop installation by editing the Registry (Windows) or running a script (Mac) on each Desktop. See Turn off dashboard extensions.
Example deployment scenarios
Using the installation settings, you can deploy Tableau Desktop in several ways.
-
Allow all extensions - In this deployment scenario, you choose to trust Tableau authors to select the Tableau Trusted extensions and Network-enabled extensions they want to use. If you want to empower your Tableau Desktop users with the greatest flexibility, use the default installation settings. Using the default settings, Tableau Desktop users have unrestricted access to Tableau Trusted and Network-enabled extensions. The default settings are:
DISABLEEXTENSIONS=0andDISABLENETWORKEXTENSIONS=0. See Install Tableau Desktop from the Command Line.Only allow Tableau Trusted extensions - In this scenario, you entrust Tableau extension services to appropriately review, deploy and curate extensions that are for broad community use, but you aren't sure about Network-enabled extensions and want to prevent their use at this time. To turn off support for Network-enabled extensions, set the
DISABLENETWORKEXTENSIONSproperty (DISABLENETWORKEXTENSIONS=1). Keep the default setting for enabling extensions (DISABLEEXTENSIONS=0). See Install Tableau Desktop from the Command Line. -
Only allow Sandboxed extensions - In this scenario, you might have used Sandboxed extensions before and feel they are safe to use,
but you aren't ready to update your policy to enable broader use for Tableau-built and Tableau trusted partner-built extensions; nor do you want to change policy to allow Network-enabled extensions. You only want to permit Sandboxed extensions to be used as they have been, and want to prevent their use of all other forms of Tableau Trusted and network-enabled extensions. To turn off support for Network-enabled extensions, Tableau-built extensions and Tableau Trusted partner-built extensions: set theDISABLENETWORKEXTENSIONSproperty (DISABLENETWORKEXTENSIONS=1),DISABLETABTRUSTEDEXTENSIONSproperty (DISABLETABTRUSTEDEXTENSIONS=1),DISABLE3PTRUSTEDEXTENSIONSproperty (DISABLE3PTRUSTEDEXTENSIONS=1). Keep the default setting for enabling extensions (DISABLEEXTENSIONS=0). See Install Tableau Desktop from the Command Line. -
No extensions allowed - In this scenario, you don't want to allow users to use extensions of any type. In this case, turn support for all extensions off by using the
DISABLEEXTENSIONSproperty (DISABLEEXTENSIONS=1). See Install Tableau Desktop from the Command Line .
Use a combination of settings You might have some users who need and should have unrestricted access to all extensions, and others for whom access to Sandboxed extensions is sufficient, and then finally a set of users who need no access to extensions at all. Because the extension options are set per desktop, you can configure your deployment for specific users and their use cases.
Web authoring - If Tableau Server or Tableau Cloud are available for your users, they can use web authoring to access extensions. In web authoring, the server or site settings for extensions apply. In this scenario, the server and site administrators can determine which extensions to allow users access to. This is managed based on server and site extension settings, which include Tableau Trusted extension options and the extension safe list for explicit Network-enabled extensions.
Recommendations for Tableau Server and Tableau Cloud
If your users have access to Tableau Server or Tableau Cloud, you can use the built-in security controls to put limits and restrictions on the extensions that can be used and under what circumstances. If you've turned off extensions on Tableau Desktop, you can still allow users to add extensions in web authoring, but you can limit the number of extensions that can be used to just ones you approve to run.
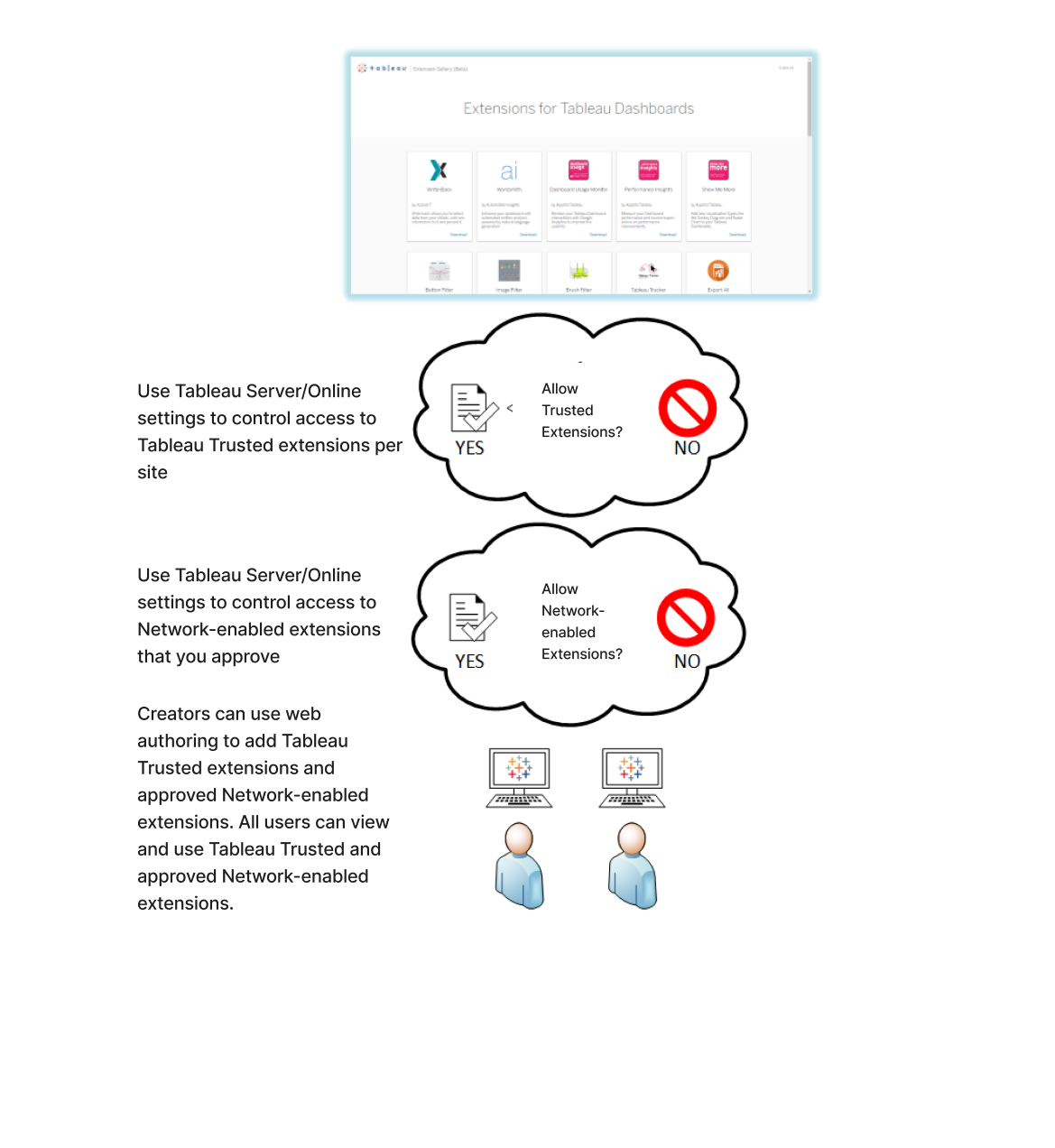
Allow Tableau Trusted extensions and the Network-enabled extensions on the safe list
Starting with Tableau 2025.3, Tableau allows some Tableau Trusted extensions to run by default. This means that Sandboxed extensions and Tableau-built extensions are elevated for use, whereas Tableau Trusted Partner-built extensions can be enabled by the administrators. While we encourage use of all Tableau Trusted extensions, as we do with our environments like Tableau Public, we ultimately feel it is critical for administrators to define the policy relevant for their deployments.
Network-enabled extensions aren't allowed unless they've been added to the safe list. Administrators can edit the settings and add Network-enabled extensions to the safe list for the site (Settings > Extensions > Enable specific Extensions).
Note To make the safe list the default behavior for extensions in Tableau 2018.2 and Tableau 2018.3, you must change the settings for the site. On the Extensions settings page, under Default behavior for Extensions, clear the Enable unknown extensions... option. In Tableau Server 2019.1, Tableau 2019.2, and Tableau 2019.3, by default, no extensions are allowed to run unless they've been added to the safe list.
Checklist for the safe list:
- Does the extension come from a source that you know and trust?
- Check the URL of the extension. Does the URL look suspicious or contain dubious domain names?
- Does the extension require access to full (underlying data) or summary data? See Understand data access.
- Test the extensions before allowing broad use. See Test extensions for security. See Test Network-enabled extensions for security.
Add extensions to the safe list:
Block specific extensions from running on Tableau Server
On Tableau Server, you can block specific extensions by adding their URL to the block list. This is useful if you have multiple sites that are configured differently for extensions. For example, if you have a test site where you want to be able to test internal or third-party extensions, you might have enabled the default behavior for extensions, where unlisted extensions are allowed to run provided they do not access the underlying data in the workbook. Adding an extension to the block list prevents it from inadvertently being used on the test site.
- Add the URL of the extensions that you don't want to allow to the blocked list. This option is only available on Tableau Server. See Block specific extensions.
Turn off extensions for a site
By default, extensions are enabled on Tableau Server and Tableau Cloud. On Tableau Server, the server administrator can turn off extensions for a site. On Tableau Cloud, the site administrator can turn off extensions for the site. On Tableau Server, the server administrator can turn off extensions completely, which overrides the site settings. You should not have to change this setting on the server or for the site, as you can control the Network-enabled extensions that you want to allow on the safe list. You can also control the settings for Tableau Trusted extensions, where Sandboxed extensions and Tableau-built extensions are allowed by default.
- To disable extensions on a site (Tableau Server, Tableau Cloud), change the site settings that enables users to run extensions on the site. See Control extensions use.
Show or hide user prompts to run Network-enabled extensions
When you add a Network-enabled extension to the safe list, you can configure whether users see prompts by default when they are adding the extension to a dashboard, or when they are interacting with a view that has the extension. The prompt tells users details about the Network-enabled extension and whether the extension has access to full data. The prompt gives users the ability to allow or deny the extension from running. You can hide this prompt from users, allowing the extension to run immediately. When enabled for a site, Sandboxed extensions are allowed by default and do not prompt users.
Turn off all or some Tableau Trusted extensions
Starting in Tableau 2025.3, Tableau allows some Tableau Trusted extensions to run on Tableau Server and Tableau Cloud by default. Sandboxed extensions and Tableau-built extensions are elevated for use, whereas Tableau Trusted Partner-built extensions can be enabled by the administrators. Sandboxed extensions run in a protected environment and are hosted by Tableau. Tableau-built extensions are developed and maintained by Tableau and hosted by Tableau. Tableau Trusted Partner-built extensions are developed and maintained by third-party partner developers, but have their solutions and updates reviewed and hosted by Tableau for availability and scale.
Administrators can control whether to let users run all, some, or none of the Tableau Trusted extensions on a site. Trusted extensions don't need to be added to the safe list. When Tableau Trusted extensions are allowed, users are able to freely add Tableau Trusted extensions to workbooks and are able to open and use workbooks that contain Tableau Trusted extensions. If you need to block a Tableau Trusted extension, please reach out to Tableau to inquire about the specific extension URL to add to the Server block list.
Server administrators can add any extension to their deployment global block list. If you need to turn off Tableau Trusted extensions completely, you can change the default setting for the site. If you change the default setting for Tableau Trusted extensions, only the extensions that are on the safe list are allowed to run.
