Domain Trust Requirements for Active Directory Deployments
When you run Tableau Server in an Active Directory environment across multiple domains (either in the same Active Directory forest or in different forests), some Tableau functionality is dependent on the trust relationship between the domains. For example, some administrators manage users in domains that are separate from where they deploy server applications, such as Tableau Server. In other organisations, a Tableau Server deployment might be shared with external partners or with different partners in the organisation. Finally, Windows-authenticated data sources, such as SQL Server, MSAS, or Oracle, that Tableau Server connects to may also be in other domains.
If it's feasible, we recommend configuring two-way trust between all domains that interact with Tableau Server. If this is not possible, Tableau Server can be configured to support user authentication where a one-way trust has been configured. In this case, a one-way trust between domains is supported when the domain in which Tableau Server is installed is configured to trust the domain where user accounts reside.
The following illustration shows one-way trust between the domain where Tableau Server is installed and the domain where user accounts reside:
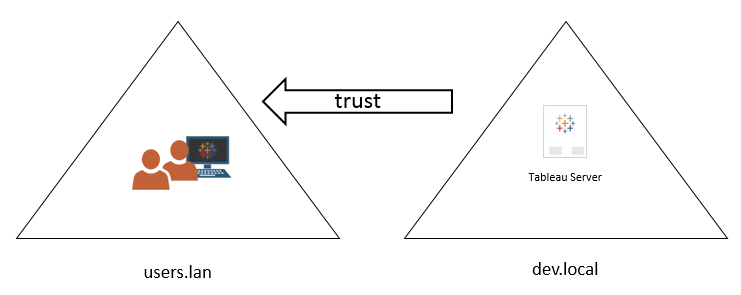
In this scenario, Tableau Server is in the dev.local domain, and users from the users.lan Active Directory domain are imported into Tableau Server. A one-way trust is required for this scenario; specifically, the dev.local domain is configured to trust the users.lan domain. Users in the users.lan domain can access Tableau Server in the dev.local with their normal Active Directory credentials. However, you may need to update the domain nickname on Tableau Server before users log on with the nickname. Refer to the Tableau Knowledge Base(Link opens in a new window) for more information.
When you configure Tableau Server for this scenario, specify the primary user domain during installation. See Configure Initial Node Settings. To ensure that Tableau Server can connect to other Active Directory domains, you must also specify other domains that Tableau Server connects to by setting the wgserver.domain.accept_list option with TSM. For more information, see wgserver.domain.accept_list.
Duplicate bind accounts for domain trust
Tableau Server on Linux relies on JDK's LDAP implementation that uses a simple bind to authenticate with Active Directory. Simple bind is not domain-aware and as a result, does not support a cross-domain bind. When you set up the initial identity store, you must supply the bind account that you will use to authenticate to Active Directory.
To enable cross-domain trust and directory look-ups, you must duplicate this bind account in every target domain. Each bind account in each domain must use the same username (sAMAccountName or dn) and password.
Kerberos single sign-on is supported in this one-way trust scenario.
Review User Management in Deployments with External Identity Stores to understand how multiple domains, domain naming, NetBIOS, and Active Directory user name format influence Tableau user management.
Connecting to live data in one-way trust scenarios
In the one-way trust scenario, users connecting to Tableau Server can connect to live data that's hosted in the cloud or on any other data source on premises that does not rely on Windows authentication.
Data sources that require Windows-authentication might have additional authentication requirements that complicate the scenario, or that can even prevent Tableau Server users from connecting. This is because Tableau Server uses
