Configure OAuth for Snowflake Connections
There are multiple ways you can configure OAuth for Snowflake connections, depending on which version of Tableau you are using and how many sites you are updating. This topic covers configuration for each available option.
- For all versions of Tableau up to and including version 2024.1, the Tableau Snowflake connector by default uses an OAuth proxy hosted in AWS (GALOP), which uses a common client ID and secret.
- Starting with Tableau 2020.4, you can optionally configure Tableau Server to use a new OAuth service that runs in the same location as that instance of Tableau. This requires providing your own client ID and secret, which is referred to as custom OAuth.
- Starting in 2024.2, the GALOP proxy will be deprecated and the instructions below for setting up custom OAuth will be required, as it will now use the local OAuth service for authentication.
- For Tableau Desktop and Tableau Cloud versions 2024.3 and beyond, you can configure a third-party IdP (external OAuth) for Snowflake. For more information, see External OAuth for Snowflake.
The benefits provided by Custom OAuth include:
Improved security
You can use OAuth in isolated environments that cannot connect to the OAuth Proxy (GALOP).
You don't have to safe-list the GALOP IP addresses to run the OAuth flow in AWS PrivateLink or Azure Private Link VPCs.
Register OAuth Client With Snowflake
To use a custom OAuth setup in Tableau Server, you must first register your OAuth client and obtain a Client ID and Client Secret to complete the configuration. For Tableau Server versions 2024.2 and later, this step is required, regardless of which configuration option you are using. To register a custom OAuth client with Snowflake, follow the steps described in Configure Snowflake OAuth for Custom Clients(Link opens in a new window).
After you register, you’ll use the following Snowflake parameters to configure Tableau Server:
- Account instance URL
- Client ID
- Client secret
- Redirect URL
Note: The Redirect URL is the same when entered both on the Snowflake and Tableau sides. The format is:
https://your_server_url.com/auth/add_oauth_token
For example, https://example.com/auth/add_oauth_token
Option 1: Configure OAuth for Snowflake Connections using TSM
We recommend using this option when you need to update several sites at once.
Note: This configuration option is not available for use on Tableau Cloud.
(Versions 2024.1 and earlier) On the Tableau Server computer, run the following command to enable the Snowflake OAuth service:
tsm configuration set -k native_api.enable_snowflake_privatelink_on_server -v trueNote: For versions 2024.2 and newer, skip step 1 regardless of whether a Snowflake private connection is being used or not.
Copy, paste, and customize the following command in a text editor:
Note: If you're making these configuration changes in Tableau Server 2021.1 and later, note that the format of the oauth.snowflake.clients value has changed.
tsm configuration set -k oauth.snowflake.clients -v " [{\"oauth.snowflake.instance_url\":\"https://account.snowflakecomputing.com\", \"oauth.snowflake.client_id\":\"client_id_string\", \"oauth.snowflake.client_secret\":\"client_secret_string\", \"oauth.snowflake.redirect_uri\":\"http://your_server_url.com/auth/add_oauth_token\" }]"The
oauth.snowflake.clientskey takes an array of key pairs. Each element in the key pair must be encapsulated by double quotes. Double quotes must be escaped as\".To specify multiple account instance URLs, separate each additional OAuth client wrapped in braces ({}) with a comma (,), as in this example:
tsm configuration set -k oauth.snowflake.clients -v " [{\"oauth.snowflake.instance_url\":\"https://account.snowflakecomputing.com\",\"oauth.snowflake.client_id\":\"client_id_string1\",\"oauth.snowflake.client_secret\":\"client_secret_string1\",\"oauth.snowflake.redirect_uri\":\"http://your_server_url.com/auth/add_oauth_token\" },{\"oauth.snowflake.instance_url\":\"https://account2.snowflakecomputing.com\",\"oauth.snowflake.client_id\":\"client_id_string2\",\"oauth.snowflake.client_secret\":\"client_secret_string2\",\"oauth.snowflake.redirect_uri\":\"http://your_server_url.com/auth/add_oauth_token\" }]"Replace the values for each key:
- Account instance URL:
oauth.snowflake.instance_url - Client ID:
oauth.snowflake.client_id - Client secret:
oauth.snowflake.client_secret - Redirect URL:
oauth.snowflake.redirect_uri
Note: Before running the command, verify the syntax carefully. TSM won’t validate this input.
Copy the command into TSM CLI and run the command.
- Account instance URL:
Enter the following command to apply the changes:
tsm pending-changes applyIf the pending changes require a server restart, the
pending-changes applycommand will display a prompt to let you know a restart will occur. This prompt displays even if the server is stopped, but in that case, there is no restart. You can suppress the prompt using the--ignore-promptoption, but this does not change the restart behaviour. If the changes do not require a restart, the changes are applied without a prompt. For more information, see tsm pending-changes apply.
Option 2: Configure OAuth for Snowflake Connections by Site
Note: This option is also available for Tableau Cloud starting with version 2024.2.
You can configure a custom Snowflake OAuth client at the site level by using the Tableau Server UI.
Consider configuring a custom OAuth client to 1) override an OAuth client if configured for the server or 2) enable support for securely connecting to data that requires unique OAuth clients.
When a custom OAuth client is configured, the site-level configuration takes precedence over any server-side configuration and all new OAuth credentials created use the site-level OAuth client by default. No Tableau Server restart is required for the configurations to take effect.
Important: Existing OAuth credentials established before the custom OAuth client is configured are temporarily usable but both server administrators and users must update their saved credentials to help ensure uninterrupted data access.
1: Prepare the OAuth client ID, client secret and redirect URL
Before you can configure the custom OAuth client, you need the information listed below. After you have this information prepared, you can register the custom OAuth client for the site. For more information, see the section Register OAuth Client With Snowflake above.
OAuth client ID and client secret: First register the OAuth client with the data provider (connector) to retrieve the client ID and secret generated for Tableau Server.
Redirect URL: Note the correct redirect URL. You will need this during the registration process in Step 2 below.
https://<your_server_name>.com/auth/add_oauth_token
For example, https://example.com/auth/add_oauth_token
2: Register the OAuth client ID and client secret
Follow the procedure described below to register the custom OAuth client to the site.
(Versions 2024.1 and earlier) On the Tableau Server computer, run the following two commands to enable the Snowflake OAuth service:
tsm configuration set -k native_api.enable_snowflake_privatelink_on_server -v truetsm pending-changes applyNote: For versions 2024.2 and newer, skip step 1 regardless of whether a Snowflake private connection is being used or not.
Sign in to your Tableau Server site using your admin credentials and navigate to the Settings page.
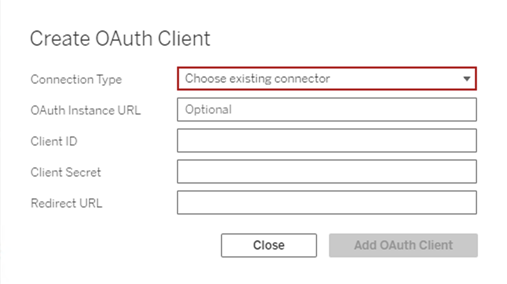
Under OAuth Clients Registry, click the Add OAuth Client button.
Enter the required information, including the information from Step 1 above:
For Connection Type, select the connector whose custom OAuth client you want to configure.
OAuth Instance URL is required if multiple OAuth clients are being registered. Otherwise, it is optional.
For Client ID, Client Secret and Redirect URL, enter the information you prepared in Step 1 above.
Click the Add OAuth Client button to complete the registration process.
(Optional) Repeat step 3 for all supported connectors.
- Click the Save button at the bottom or top of the Settings page to save changes.
3: Validate and update saved credentials
To help ensure uninterrupted data access, you (and your site users) must delete the previous saved credentials and add it again to use the custom OAuth client for the site.
Navigate to your My Account Settings page.
Under Saved Credentials for Data Sources, do the following:
Click Delete next to the existing saved credentials for the connector whose custom OAuth client you configured in Step 2 above.
Next to connector name, click Add and follow the prompts to 1) connect to the custom OAuth client configured in Step 2 above and 2) save the latest credentials.
4: Notify users to update their saved credentials
Make sure you notify your site users to update their saved credentials for the connector whose custom OAuth client you configured in Step 2 above. Site users can use the procedure described in Update saved credentials to update their saved credentials.
