Signing In to Tableau Server Using OpenID Connect
This topic provides information about signing in to Tableau Server using OpenID Connect. The following topics provide information about configuring and using OpenID Connect with Tableau Server.
Signing In to Tableau Server Using OpenID Connect (you are here)
Signing in using OpenID Connect
After Tableau Server has been configured to use OpenID Connect, users who access the server and aren't already signed in are redirected to the IdP site, where they are prompted to sign in. Users enter the credentials that they have with the IdP. In many cases, the user is also asked to authorise the IdP to share information with Tableau Server, as in the following example:
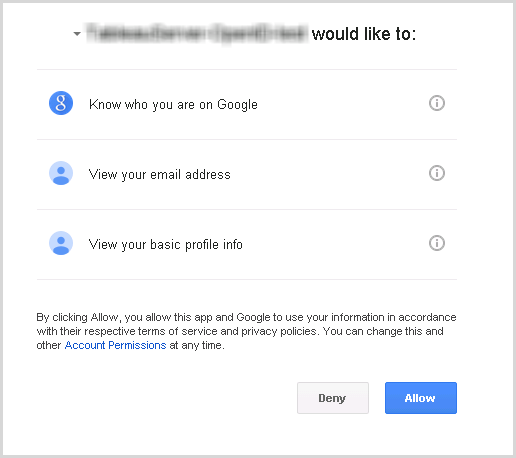
When a user signs in using OpenID Connect, the IdP sends a unique user identifier (known in OpenID as the sub value) as part of the information that's redirected to Tableau Server. This sub value is associated with the user's Tableau user identity.
Restricting sign-in to server administrators for command-line tools
Command-line tools for working with Tableau Server (tabcmd, TSM, and tableau.com) do not support sign-in using OpenID Connect. When OpenID Connect is enabled for the server, these tools still require sign-in using a Tableau Server username and password.
Even if users normally authenticate using OpenID Connect, each user has a Tableau Server username and password. This means that users could use command-line tools like tabcmd. As a security measure, you can make sure that only server administrators can use command-line tools. To do this, use tsm configuration set to set wgserver.authentication.restricted to true. When this setting is true, only server administrators can sign in to Tableau Server using a username and password; all other users must sign in to the server using a single sign-on (SSO) option like OpenID Connect. The effect is that users who are not administrators also cannot then use command-line tools. To make this change, run the following sequence of TSM commands:
tsm configuration set -k wgserver.authentication.restricted -v true
tsm pending-changes apply
