Personal Access Tokens for Tableau Cloud Manager
Personal access tokens (PATs) provide you with the ability to create long-lived authentication tokens. PATs enable you to sign in to the Tableau Cloud Manager REST API without requiring hard-coded credentials (username and password) or interactive sign-in. For more information, see Tableau Cloud Manager REST API(Link opens in a new window).
Note: Tableau Cloud Manager PATs can’t be used to sign in to the Tableau REST API, which is used to manage and change Tableau Cloud site resources.
We recommend creating PATs for automated scripts and tasks that are created with the Tableau Cloud Manager REST API:
Improve security: PATs reduce risk in the event credentials are compromised. Instead of using a username and password, users can reduce the impact of credential compromise by using a personal access token for automated tasks. If a PAT gets compromised or is used in automation that’s failing or posing a risk, you can revoke the PAT instead of rotating or revoking the user's credentials.
Manage automation: A PAT can be created for each script or task that is run. This allows you to silo and review automation tasks across your organization. Additionally, by using PATs, password resets or metadata changes (username, email, etc.) on user accounts, automation isn’t disrupted like it is when credentials are hard-coded into the scripts.
Notes:
PATs are required to make a Tableau Cloud Manager REST API sign-in request to Tableau Cloud Manager (TCM) with multi-factor authentication (MFA) enabled with Tableau authentication.
PATs aren’t used for generic client access to TCM.
PATs are automatically revoked when the TCM authentication method changes.
The first time you sign in to the Tableau Cloud Manager REST API, a PAT must be created using the TCM UI using the procedure described below or in Authentication(Link opens in a new window) in the TCM REST API Help.
Understand personal access tokens
When a personal access token (PAT) is created, it’s hashed then stored in the repository. After the PAT is hashed and stored, the PAT secret is shown once to the user and then no longer accessible after they dismiss the dialog. Therefore, users are instructed to copy the PAT to a safe place and handle it like a password.
When the PAT is used at run-time, Tableau Cloud Manager (TCM) compares the PAT presented by the user to the hashed value stored in the repository. If a match is made, then an authenticated session is started. In the context of authorisation, the TCM session that is authenticated with a PAT has the same access and privileges as the PAT owner.
About PAT expiration
Personal access tokens (PATs) expire if not used after 15 consecutive days or based on the token expiry value selected when creating the PAT, whichever comes first.
After PATs expire, they're unable to be used for authentication and removed from the cloud administrator's My Account Settings page.
Tasks for managing cloud administrator's personal access tokens
Create a PAT
This procedure requires you to copy a secret to a file. The secret is the string that you include in your automation scripts and will be used to authenticate to Tableau Cloud Manager (TCM). Handle the secret as you would a password: protect the secret and don’t share it with others.
To create a PAT, follow these steps:
Sign in to Tableau Cloud Manager as a cloud administrator.
At the top of a page, click your profile image or initials, and then select My Account Settings.
Under Personal Access Tokens, click Create Token.
Enter a descriptive name for your token in the Token Name field.
Select the token expiry date and click Create Token.
In the Personal Access Token dialog box, click Copy Secret.
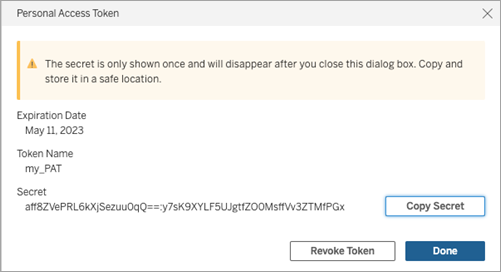
Paste the secret to a file and store the file in a safe location.
When finished, click Done.
Note: A user can have up to 104 PATs.
Revoke a PAT
Cloud administrators can revoke their PAT on their My Account Settings page using the following steps:
Sign in to Tableau Cloud Manager as a cloud administrator.
At the top of a page, click your profile image or initials, and then select My Account Settings.
Under the Personal Access Tokens section, identify the PAT that you want to revoke and then click Revoke Token.
In the Delete dialog box, click Delete.
